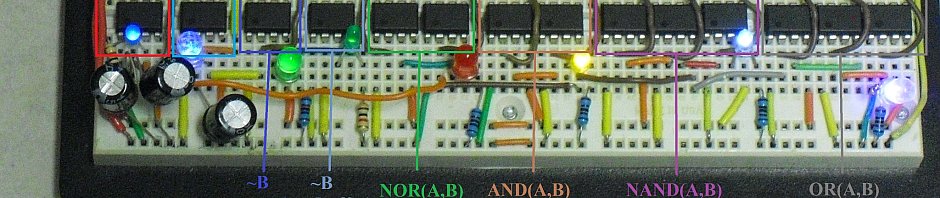
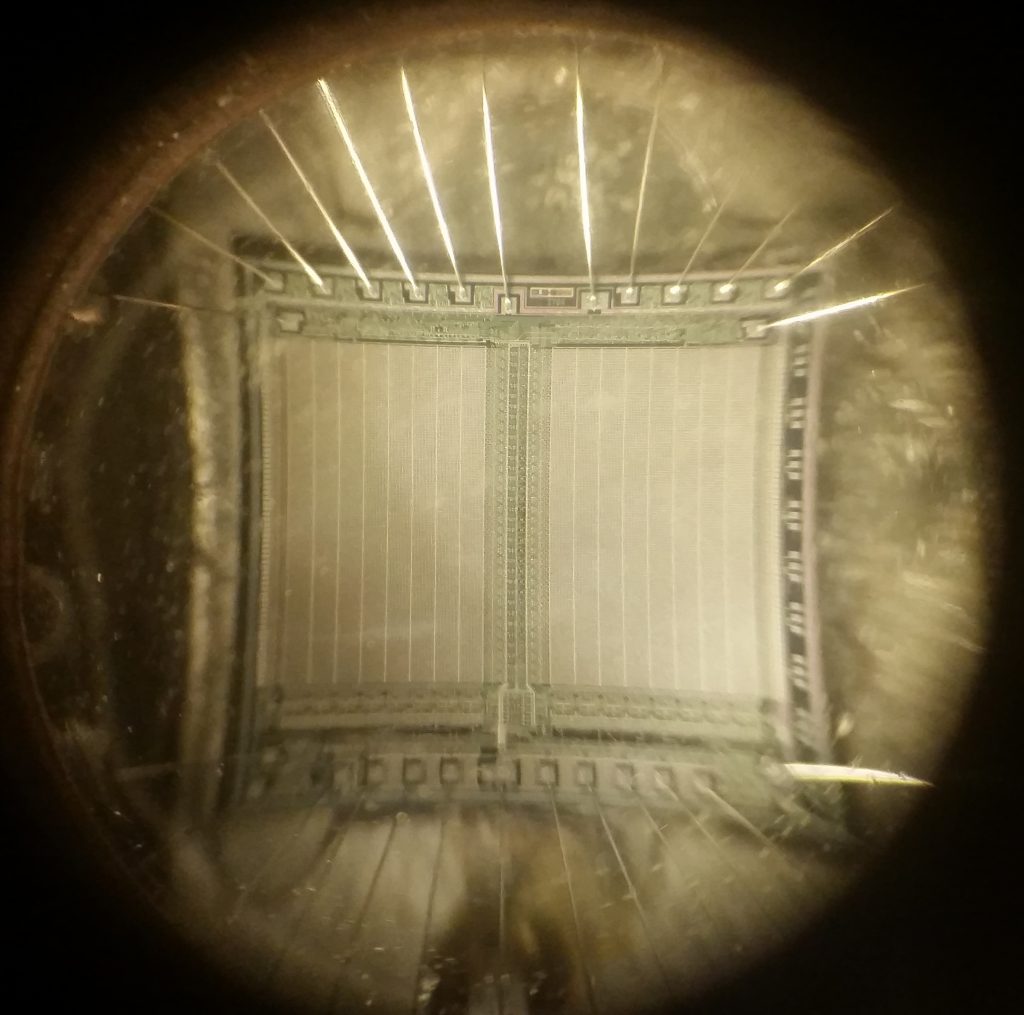
EPROMs are interesting devices. With the advent of Flash memory, they’re not in common use these days. However, they are extremely easy to integrate into hobby electronics, and can serve several functions, including a few off-label ones that I’m currently investigating.
EPROM stands for Erasable/Programmable Read-Only Memory. As the name implies, it can be erased and reprogrammed, but this is typically not done in circuit. Instead, specialized eraser and programmer units are used to reset the chips and then program them. The new semi-permanent ROM chips can then be used in a TTL circuit just like custom ROM chips; place the address on the address bus, lower ~CE, ~OE, and ~RD, and read the data from the data bus.
EPROM chips are reprogrammed in a two-step process. First, the cells are cleared by setting them to all-ones. Any covering of the optical window is removed, and the chips are subjected to ultraviolet light, which quickly resets all of the exposed memory cells to the “1” state. Programming, done in a separate device, then consists of zeroing out everything that shouldn’t be a 1, much like Michelangelo removed the marble that wasn’t part of his statues.
This is all transparent (pardon the pun) to the user; you simply “bake” the chips in the UV “oven” and then use the programmer per the directions.
Once you understand the process, though, it’s possible to try more interesting experiments. EPROMs are inherently analog devices, with analog amounts of charge stored in each cell.
In the past, others have made clever use of the inherent analog nature of EPROMs by using them to store “digilog” audio — sampled audio, stored as analog charges instead of binary representation. Certainly one of the more unique audio storage methods out there: instead of storing zeroes and ones at every address, eight analog charges were stored.
Due to their optical erasure method, EPROMs can also be used to sense light exposure. Although the data sheets state to “bake” the chips for roughly 45 minutes to an hour for erasure, I’ve found that as little as 20 to 30 seconds is often enough to at least make the chip read as erased. (It may be that longer erasure times help ensure that the 1s remain readable.)
They probably won’t be much use as imaging sensors — even if an image could be properly focused on the split halves of the die, the image would only be roughly 256 by 256, in grayscale. Not exactly high definition. But they might make interesting sunlight-exposure sensors.